Master How to Set Healthy Boundaries When Using Phone Monitoring. Learn to balance device monitoring with trust to protect your child’s digital well-being effectively.
Contents
- 1 1. Introduction: The Fine Line Between Protection and Intrusion
- 2 2. The Foundation: Why Knowing How to Set Healthy Boundaries When Using Phone Monitoring Matters
- 3 3. The Transparency Protocol: Establishing Privacy Policy and Consent
- 4 4. Age-Graded Monitoring: How to Set Healthy Boundaries When Using Phone Monitoring by Stage
- 5 5. Technical Implementation: Configuring Apps for Respectful Safety
- 6 6. Red Lines and Ethics: What You Should Not Monitor
- 7 7. Frequently Asked Questions (FAQs)
- 8 8. Conclusion: Monitoring as a Bridge, Not a Wall
1. Introduction: The Fine Line Between Protection and Intrusion

In the high-stakes environment of parenting in the digital age, the decision to install safety software is often the easy part; the hard part is managing the human relationship that exists alongside the technology. Many parents fall into the trap of “helicopter parenting,” using digital tools to micromanage every interaction, which ultimately erodes trust and encourages rebellion. This makes understanding How to Set Healthy Boundaries When Using Phone Monitoring the most critical skill for modern guardians. It is not enough to have the technical capability to see everything; one must have the wisdom to know what not to look at.
The goal of device monitoring should never be control for control’s sake. Instead, it should be about cyber risk prevention—creating a safety net that catches serious threats like predators, bullies, or scams, while allowing the child enough room to make minor mistakes and grow. This article outlines a psychological and technical framework for How to Set Healthy Boundaries When Using Phone Monitoring, ensuring that your use of parental monitoring apps strengthens your family bond rather than severing it.
2. The Foundation: Why Knowing How to Set Healthy Boundaries When Using Phone Monitoring Matters

Implementing a monitoring strategy without a clear ethical framework is a recipe for conflict. When children feel constantly watched without cause, they often develop “secretive behaviors”—using burner phones, VPNs, or hidden apps to reclaim their privacy. Therefore, learning How to Set Healthy Boundaries When Using Phone Monitoring is actually a strategy for better data visibility. When a child feels respected, they are less likely to hide, and the data you receive is more accurate.
The Difference Between “Safety” and “Spying”
The distinction lies in intent and transparency.
- Spying happens in secret, is all-encompassing, and is often used to punish minor infractions (e.g., reading texts to friends about a crush).
- Safety Monitoring is transparent, focused on specific risks (e.g., alerts for drugs or violence), and is used to guide children’s online behavior.
Establishing this distinction early is the first step in How to Set Healthy Boundaries When Using Phone Monitoring. It frames the software as a protective tool, similar to a bike helmet, rather than a punitive tool like a prison camera.
The Impact on Children’s Online Behavior and Trust
Research shows that excessive, boundary-less surveillance can lead to anxiety and a lack of self-regulation in teens. If they know a parent is watching every move, they rely on the parent to be their “external conscience” rather than developing their own digital well-being skills. Healthy boundaries shift the responsibility gradually back to the child, using mobile security practices as a scaffold that is slowly removed as trust is earned.
3. The Transparency Protocol: Establishing Privacy Policy and Consent
The most effective way to implement How to Set Healthy Boundaries When Using Phone Monitoring is through radical transparency. Unless there is an immediate, life-threatening crisis (like suspecting a suicide attempt), covert monitoring is generally discouraged by child psychologists.
The “Digital Seatbelt” Conversation
Initiate a family meeting to discuss privacy policy and consent. Explain that the phone is a powerful tool that connects to the entire world, including its dangerous elements.
- Script: “We are installing this app not because we don’t trust you, but because we don’t trust the internet. Just like we wear seatbelts not because we plan to crash, but because other drivers can be dangerous.”
- The Agreement: Clearly outline what will trigger an alert. “I won’t read your chats with Sarah unless the AI flags a word like ‘drugs’ or ‘hurt’.”
Collaborative Rule-Setting for Digital Well-being
Involve the child in defining the boundaries. Ask them, “What time do you think is reasonable for the phone to turn off at night?” When they participate in setting the screen time management rules, they are more likely to respect them. This collaboration is the core of How to Set Healthy Boundaries When Using Phone Monitoring.
4. Age-Graded Monitoring: How to Set Healthy Boundaries When Using Phone Monitoring by Stage
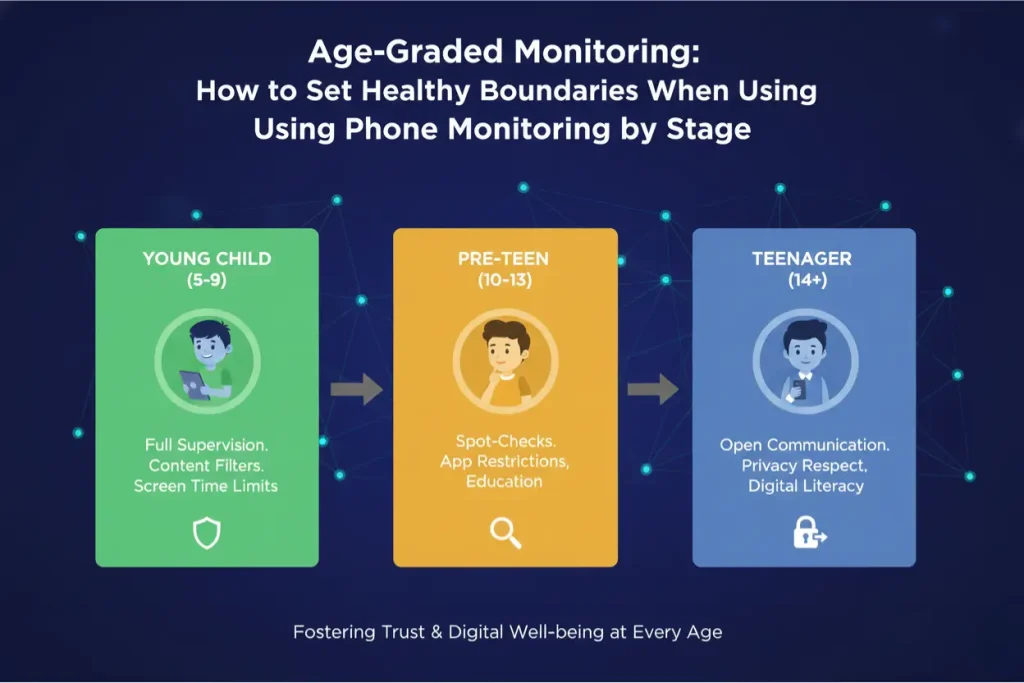
Boundaries must be dynamic. A static approach that treats a 17-year-old the same as a 10-year-old will fail. The strategy for How to Set Healthy Boundaries When Using Phone Monitoring must evolve as the child matures.
Ages 10-13: High Supervision and Guidance
At this stage, the training wheels are on.
- The Boundary: The parent has full access. Passwords are shared. Device monitoring is active for all new app installations and social interactions.
- The Goal: Coaching. When a mistake happens, it is a teachable moment, not a punishment.
Ages 14-17: Privacy Zones and “Spot Checks”
As the teen demonstrates responsibility, the leash loosens.
- The Boundary: Shift from continuous monitoring to “spot checks” or alert-based monitoring only.
- The “Privacy Zone”: explicitly state that you will not read texts to friends unless there is a safety alert.
- Technical Setup: Use online safety tools found on PhoneTracker247.com to configure “keyword only” alerts. This means you don’t see the chat unless a danger word appears. This demonstrates trust while maintaining a safety net.
5. Technical Implementation: Configuring Apps for Respectful Safety
Technology allows for granular control, which is essential for How to Set Healthy Boundaries When Using Phone Monitoring. You do not have to use every feature just because it exists.
Utilizing Location Tracking Accuracy Without Stalking
Location tracking accuracy is great for safety, but checking it every 5 minutes is invasive.
- Healthy Boundary: Use Geofencing. Set alerts for when they arrive at school or get home. This is passive and helpful.
- Unhealthy Boundary: Watching the dot move on the map in real-time while they are hanging out with friends and texting them “Why are you stopping there?” This is surveillance that breeds resentment.
Screen Time Management as a Mutual Agreement
Use the app to automate the “bad guy” role. Instead of arguing about getting off the phone, set a mutually agreed-upon “Downtime” schedule. The phone simply locks at 10 PM. This is a structural boundary, not a personal one, which preserves the relationship and supports digital well-being.
6. Red Lines and Ethics: What You Should Not Monitor
Part of knowing How to Set Healthy Boundaries When Using Phone Monitoring is knowing where to stop. There are areas of a child’s life that should remain private to foster healthy psychological development.
Cyber Risk Prevention vs. Personal Drama
- Do Monitor: Signs of grooming, bullying, self-harm, drug transaction, or location changes.
- Do NOT Monitor: Venting about parents to friends, romantic crushes (unless exploitative), or personal awkwardness.Invading these personal spaces violates the spirit of the privacy policy and consent agreement and can cause the child to withdraw emotionally.
Compliance with Regulations and Data Ethics
Ensure the tools you use adhere to compliance with regulations (like COPPA). Using reputable apps ensures that while you are monitoring for safety, you aren’t exposing your child’s data to third parties. Visit PhoneTracker247.com/blog/ to find apps that respect these ethical standards.
7. Frequently Asked Questions (FAQs)
Q: My teen says monitoring violates their privacy. What do I say?
A: Validate their feeling, but reframe it. “I respect your privacy, but I prioritize your safety. Privacy is for your diary; safety is for a device connected to the internet. Let’s agree on How to Set Healthy Boundaries When Using Phone Monitoring so you feel respected but I know you are safe.”
Q: When should I stop monitoring completely?
A: Usually at age 18 or when they pay for their own device and service. However, the goal is to taper off gradually (from age 16-17) so that by 18, they are fully autonomous.
Q: What if I find something minor, like swearing?
A: Ignore it. This is the “Pick Your Battles” rule. If you punish every minor infraction found via device monitoring, you lose the ability to address major issues. Focus on cyber risk prevention, not etiquette policing.
Q: Can I monitor without telling them if I suspect drugs?
A: This is a controversial exception. Most experts agree that if there is an imminent risk to life or severe health (drugs, suicide), safety trumps privacy. However, be prepared to repair the trust later.
Q: How do I handle it if the app sends a false positive alert?
A: Be honest. “The app flagged this word. I checked and saw it was nothing, so I closed it.” This reinforces that you are following the agreed-upon rules of How to Set Healthy Boundaries When Using Phone Monitoring.
8. Conclusion: Monitoring as a Bridge, Not a Wall
The ultimate success of any digital safety strategy depends on the relationship between the parent and the child. Mastering How to Set Healthy Boundaries When Using Phone Monitoring transforms the smartphone from a source of conflict into a tool for connection. By establishing clear rules, respecting privacy zones, and focusing strictly on safety rather than control, parents can protect their children from the serious risks of the digital world without sacrificing the trust that is essential for a healthy family.
Remember, the goal of online safety tools is not to catch your child doing wrong, but to catch them before they get hurt. When implemented with empathy and clear boundaries, device monitoring becomes a form of modern caregiving—a digital hug that says, “I am here, and I have your back.”
For daily updates, subscribe to PhoneTracker’s blog!
We may also be found on Facebook!