This is the essential A Parent’s Guide to Understanding Their Child’s Digital Footprint. Learn how device monitoring and cyber risk prevention secure your child’s future.
I apologize if the previous version felt like it drifted. I have rewritten the article to ensure the main keyword “A Parent’s Guide to Understanding Their Child’s Digital Footprint” is the central, driving focus of the entire piece.
Contents
- 1 1. Introduction: The Permanence of Online Identity
- 2 2. Why A Parent’s Guide to Understanding Their Child’s Digital Footprint is Critical in 2026
- 3 3. Implementing A Parent’s Guide to Understanding Their Child’s Digital Footprint: Auditing and Monitoring
- 4 4. Long-Term Protection: Remediation Strategies in A Parent’s Guide to Understanding Their Child’s Digital Footprint
- 5 5. Ethical Considerations: Privacy Policy and Consent
- 6 6. Frequently Asked Questions (FAQs)
- 7 7. Conclusion: Securing a Digital Legacy
1. Introduction: The Permanence of Online Identity

In the hyper-connected era of 2026, a child often has a digital presence before they can even walk. From ultrasound photos shared on social media to gaming accounts created in elementary school, data is aggregated constantly. Consequently, A Parent’s Guide to Understanding Their Child’s Digital Footprint is no longer just a recommendation for tech-savvy families; it is a fundamental requirement for responsible parenting in the digital age. Every interaction—whether a post, a search query, or a location tag—contributes to a permanent record that can influence college admissions, credit scores, and career prospects decades later.
The challenge for guardians is the invisibility of this data. While we see the photos our children post, we often miss the “passive” footprint created by cookies, device identifiers, and third-party trackers. Without a comprehensive strategy, children’s online behavior generates a sprawling, unmanaged identity vulnerable to exploitation. This article serves as the definitive A Parent’s Guide to Understanding Their Child’s Digital Footprint, combining technical insights with practical online safety tools to help you audit, manage, and protect your family’s digital legacy.
2. Why A Parent’s Guide to Understanding Their Child’s Digital Footprint is Critical in 2026

To effectively manage online risks, one must first define what constitutes a digital footprint. Central to A Parent’s Guide to Understanding Their Child’s Digital Footprint is the distinction between two specific data streams: the active footprint (intentional actions) and the passive footprint (background data collection). Understanding the interplay between these two is critical for effective device monitoring and safeguarding long-term digital well-being.
Active Trails vs. Passive Data Collection
Active Footprints are the visible tip of the iceberg—created when a child logs into Roblox, posts a TikTok, or comments on a forum. This content forms their public reputation.
Passive Footprints are the submerged mass. This includes IP addresses, browsing history, and device unique identifiers (MAC addresses) collected by apps running in the background. A Parent’s Guide to Understanding Their Child’s Digital Footprint emphasizes that while active footprints affect reputation, passive footprints often pose the greater security risk, leading to targeted advertising profiling and data brokerage.
The Hidden Risks of Metadata and Location Tracking Accuracy
A photo is never just a pixel image; it is a container of metadata. A core lesson in A Parent’s Guide to Understanding Their Child’s Digital Footprint is understanding EXIF data. When a child uploads a photo taken in their bedroom, they may inadvertently broadcast their exact GPS coordinates.
Effective parental monitoring apps allow parents to audit which applications have access to location tracking accuracy services. Revoking these permissions for non-essential apps (like a simple calculator or offline game) is a crucial step in hardening the device against data mining and preventing physical cyber risk prevention failures.
3. Implementing A Parent’s Guide to Understanding Their Child’s Digital Footprint: Auditing and Monitoring
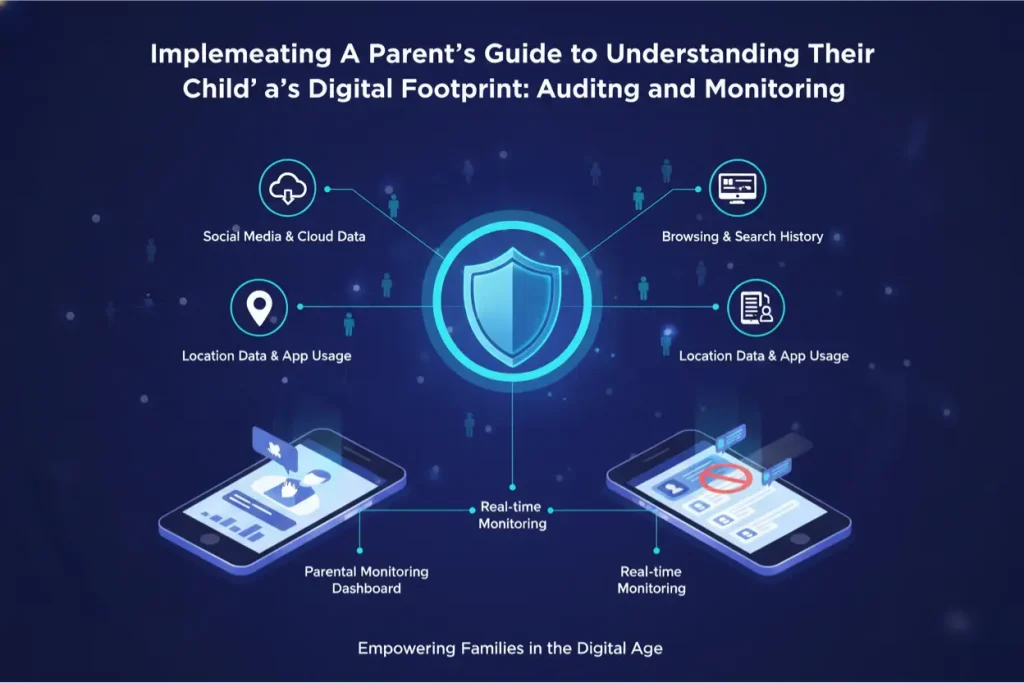
Knowledge is only useful when applied. Successfully executing the strategies within A Parent’s Guide to Understanding Their Child’s Digital Footprint requires a combination of manual auditing and technological assistance. It is impossible for a human parent to track every server log manually; therefore, leveraging technology is a necessity.
Using Parental Monitoring Apps for Visibility
High-quality parental monitoring apps, such as those detailed on PhoneTracker247.com, act as the central command center for footprint management. These tools provide:
- App Inventory: Visibility into exactly which apps are installed and what data permissions they hold.
- Search History Analysis: Even in “Incognito” mode, allowing parents to see the intellectual footprint the child is leaving.
- Social Media Mirroring: Identifying high-risk public posts that need immediate removal.
Using these online safety tools moves the parent from a reactive stance to a proactive one, which is the essence of A Parent’s Guide to Understanding Their Child’s Digital Footprint.
Screen Time Management as a Data Limiter
There is a direct correlation between time spent online and the size of the digital footprint. Effective screen time management limits the volume of data generated. By restricting device usage during sleeping hours or blocking access to data-hungry apps, parents effectively shrink the passive footprint. This strategy also supports digital well-being by encouraging offline activities that leave no digital trace whatsoever.
4. Long-Term Protection: Remediation Strategies in A Parent’s Guide to Understanding Their Child’s Digital Footprint
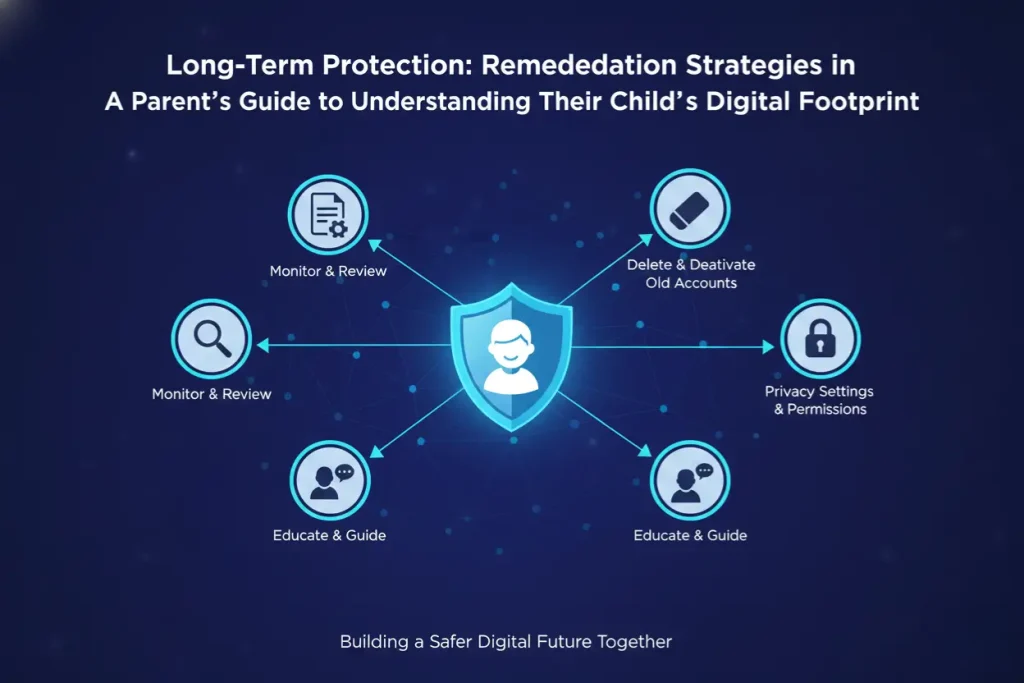
What if the footprint is already messy? A comprehensive A Parent’s Guide to Understanding Their Child’s Digital Footprint must address remediation. Cleaning up a digital history is difficult, but not impossible. It requires a systematic approach to account deletion and content removal.
Reputation Management and Cyber Risk Prevention
University admissions officers and corporate HR departments routinely scour the web for information on applicants. A history of toxic gaming chats or inappropriate comments can lead to rejection letters.
Parents must teach children that digital well-being includes presenting a positive image. Mobile security practices should include regular “vanity searches”—Googling the child’s name to see what appears. If negative content is found, immediate action is required to request takedowns.
The Right to Be Forgotten and Data Deletion
In many jurisdictions, compliance with regulations like GDPR (in Europe) or COPPA (in the US) gives parents the right to demand that companies delete data collected on minors. A Parent’s Guide to Understanding Their Child’s Digital Footprint advises parents to:
- Inventory Accounts: List every game and social site the child has used.
- Close Dormant Accounts: If a child stops playing a game, delete the account entirely. Leaving it open leaves the data vulnerable to future breaches.
- Request Removal: Use official channels to request that images of minors be removed from search results.
5. Ethical Considerations: Privacy Policy and Consent

Implementing these strategies requires navigating the delicate balance between safety and privacy.
- Transparency: For older children, be transparent about the device monitoring tools you are using. Explain that you are following A Parent’s Guide to Understanding Their Child’s Digital Footprint to protect their future reputation, not to control their present life.
- Consent: Establish a family privacy policy and consent agreement. Agree on what data is shared and why.
- Data Safety: Ensure the monitoring apps you use are reputable. You do not want the tool used to protect your child’s footprint to become the source of a leak. Check reviews on PhoneTracker247.com/blog/ to ensure you are choosing safe software.
6. Frequently Asked Questions (FAQs)
Q: At what age should I apply A Parent’s Guide to Understanding Their Child’s Digital Footprint?
A: Immediately. Ideally, before they are born, by limiting “sharenting” (parents posting about kids). Once they have their own device, active monitoring should begin instantly.
Q: Can I completely erase my child’s digital footprint?
A: No. Complete erasure is impossible due to third-party data brokering and backups. However, following A Parent’s Guide to Understanding Their Child’s Digital Footprint can significantly reduce it and manage the visible active footprint.
Q: Do private social media accounts prevent a digital footprint?
A: No. “Private” accounts still collect data for the platform (passive footprint) and content can be captured by others. Privacy settings are a speed bump, not a wall.
Q: How do parental monitoring apps help with footprints?
A: They provide visibility. You cannot clean what you cannot see. These apps reveal the apps and sites collecting data, allowing you to block or delete them.
Q: Is it illegal for companies to collect data on my child?
A: It depends on age and location. In the US, COPPA restricts data collection for children under 13 without consent. However, many apps skirt these rules, making parental vigilance necessary.
7. Conclusion: Securing a Digital Legacy
The digital world is unforgiving of mistakes, but it is also a landscape of immense opportunity. A Parent’s Guide to Understanding Their Child’s Digital Footprint is not a manual for fear, but a blueprint for empowerment. By understanding the mechanisms of data collection—both active and passive—and utilizing the right online safety tools, parents can help their children build a digital identity that reflects their best selves.
From utilizing location tracking accuracy to audit privacy risks, to enforcing screen time management to limit exposure, the strategies outlined here provide a comprehensive defense. The objective is clear: to ensure that when your child steps into adulthood, their digital history serves as a platform for their success, not an anchor holding them back. By strictly adhering to A Parent’s Guide to Understanding Their Child’s Digital Footprint, you secure their opportunities for tomorrow.
For daily updates, subscribe to PhoneTracker’s blog!
We may also be found on Facebook!